IT Asset Management
Make better decisions with real-time inventory and powerful reporting capabilities.
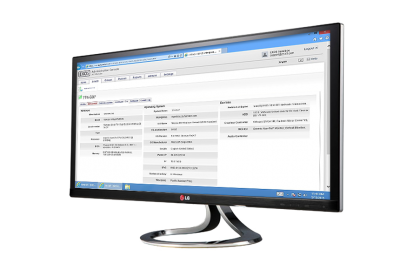
Hardware/software inventory
Collect essential ITAM data including hardware and software inventory, and network and operating system information. Extend inventory data with custom fields. Screenshot >
Reports and proof-of-compliance
Choose from pre-set report templates or create custom reports. RemoteKill® and disk encryption event logs support adherence to privacy regulation and provide crucial proof of compliance to auditors.
RiskSense™ alerts
RiskSense monitoring identifies usage patterns that may indicate impending asset theft of security lapses, such as nonreporting devices, idle equipment, and unauthorized user changes. Investigate and resolve potential asset compromises before they happen.
Data APIs
Feed EXO5 data to your helpdesk, CRM, ERP, and other enterprise applications with EXO5 data APIs. Eliminate double-entry and deliver accurate ITAM data throughout your organization.
